Know Your IT Help Maturity - 3 Keys To Improve Your Business

As businesses recover from the disruptions caused by the pandemic and try to get back to normal, 48% of them rate their internal IT help as low maturity according to a new survey conducted by the Info-Tech Research Group. Using Info-Tech's maturity ladder of 5 levels - Struggle, Support, Optimize, Expand, and Transform, most internal IT departments are in the bottom of the ladder. We see an increase by more than twice at the "struggle" level and a decrease by half at the "transform" level from the previous year.
In this article, we'll cover 3 (out of 45) key IT processes that make up the IT governance framework that every business needs to have in place. Our approach looks at three of the fundamental elements that organizations need to move up from the struggle level. For some businesses, this will require a pivot in mindset over the traditional approach to IT. By applying these key tips, along with our IT solutions checklist, you'll know what to look for, what fundamental questions to ask, and how to begin improving your business IT maturity level.
Business IT Help Level
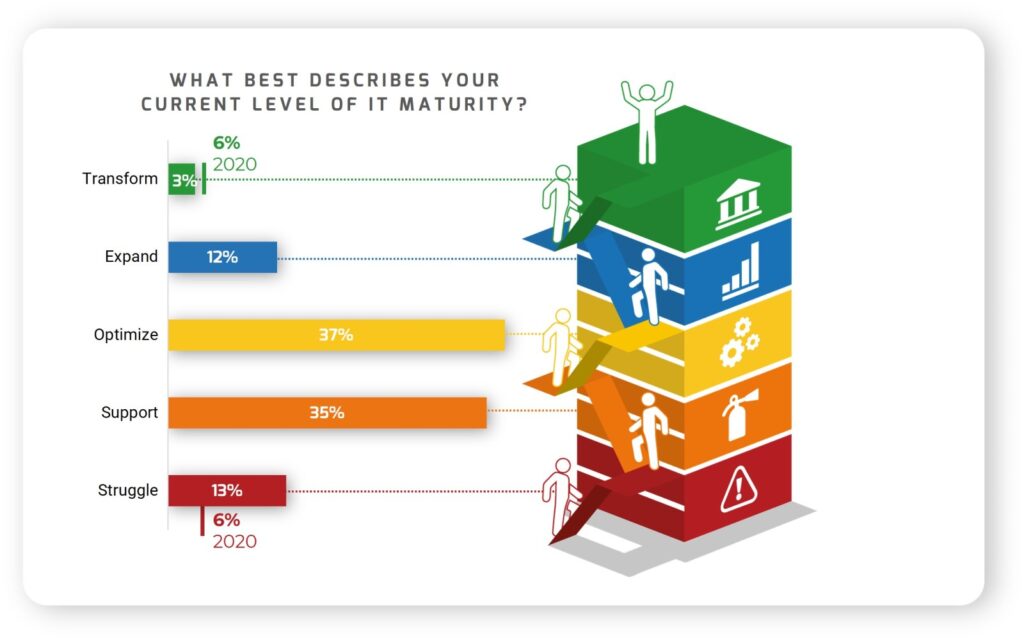
Approximately 7% of organizations will continue to do business as before the pandemic occurred, while 33% will make some minor changes in how they conduct business moving forward. With IT help maturity level going in the wrong direction, businesses will need to re-think their investment strategy in IT, including IT departments, to keep up with the pace of change.
To help organizations evaluate their IT help, here are our top 3 keys that every business needs to have in place as their foundation.
Key #1 - IT Strategy
Regardless of the company size, a business without an IT strategy is flying blind. A strategy is needed to see how the current IT infrastructure, systems, security, and processes all align with the business goals. An IT strategy is closely associated with the company's goals to support and achieve those goals. The strategy needs to work closely with the business and evolve to meet new goals and customer expectations. Without an IT strategy, a company will not know if it is hitting the mark or is way off.
A company that recognizes how an IT strategy is connected to their business goals will be better positioned than one that isn't. Below are just some of the missed opportunities for organizations without a strategy.
In this phase, it's important to evaluate how the business will achieve the operational efficiencies using internal IT help and/or IT outsourcing.
IT Maturity Level Questions
- What is your vision and how do you plan to grow your business and help your customers using IT.
- What is your investment or real cost of having an internal IT department vs desired outcome and capabilities.
- What portion of your business IT is dependent on a part-time/as-needed substitute resource (e.g., contactor).
- What are your near and long-term IT and business goals. How you plan to achieve them within your budget.
- What percentage of your cost is allocated to training your IT staff and how has it helped your business agility.
- How often is your company affected by the same unresolved issues and decrease in efficiencies.
- How has your investment helped to modernize your company's IT infrastructure, systems, and security.
- How is your Return on Investment (ROI) improving processes and increasing agility in this post-pandemic era.
Key #2 - Cybersecurity Strategy
Organizations that view their investment in IT as an integral part of doing business will need to have a Cybersecurity Strategy in place. Businesses without this strategy will need to create one that is supported from top management to all employees. The company's policy will reflect security principles defined in the strategy. If you are building an IT department instead of outsourcing to a Managed Services Provider (MSP), you will need provide employees with appropriate cybersecurity training. Employees will need to know how to respond to avoid being a victim of cyber attacks.
In this phase, you want to create a blueprint and build a culture in order to enforce your strategy. Overlooking this phase will leave your employees to act on their own and respond as they see fit to security-related situations. Below are some elements to consider as part of your Cybersecurity strategy.
Cybersecurity Strategy Elements
- Company-wide security policy that communicates roles and responsibilities for every employee and IT contractor.
- Procedure to equip your IT help with proper security training, evaluation, and frequent testing.
- Modern security protection for users working in the office or remotely.
- Software update consistency across all operating systems.
- Password encryption vault for safe password storage.
- Security auditing and reporting.
- Ongoing backup of critical data.
- Protection against ransomware attacks.
Key #3 - IT Outsourcing Strategy
Companies that view growth as part of their business model will want to have an IT Outsourcing Strategy. One reason to consider IT outsourcing is to improve operational and process efficiencies, and reduce costs for your organization. Small businesses tend not to have any IT related strategies in place. When it comes to IT, they operate their business using a traditional break-fix mentality. They use a substitute resource (e.g., IT contractor) when issues or projects come up with no long-term defined strategy.
Listed below are 4 elements to consider as part of your IT Outsourcing strategy. Gartner defines IT outsourcing as "the use of external service providers to effectively deliver IT-enabled business process, applications service, and infrastructure solutions for business outcomes." Click here for complete definition.
IT Outsourcing Strategy Elements
- Assess your current capabilities and limitations to reach your desired outcome defined by your business.
- Consider if you have the right IT solution in-house or if there is cost reductions and process efficiencies by outsourcing IT.
- What is your solution to grow IT expertise, through training internally or hiring externally.
- How equipped is your internal help or substitute resource to handle cyber attacks across your operating systems.
IT Maturity Level Checklist
We've put together a checklist of 13 key IT solutions just for you. The IT maturity level checklist is meant to help you verify that your current IT infrastructure is "up to par" to handle the expanding needs of your business and the growing risk of cyberattacks. Whether you have an internal IT department or outsourced your IT, simply provide this PDF to your team and ask them to provide what solutions are in place for each line item. Click here to learn more.

About Us
Everything IT Pros is a Managed Services Provider (MSP) and we help businesses with IT outsourcing of support and security. We offer month-to-month IT powered plans and no long-term contracts to do business. We simply go out of our way to earn your business each month and take all your daily IT functions off your plate. Our packages include a powerful 24x7x365 security and remote support for wherever you work. Contact us today to find out how to easily outsource your IT and get a help desk team that you and your employees will love.