What Is Endpoint Software? #1 Reason Why You Need It!

What Is Endpoint Software?
An endpoint today represents more than just a desktop computer; it can be a desktop, laptop, tablet, phone, and server. These devices connect to your wired and wireless network, and to the cloud to access software and services. Since every endpoint is a primary target for a cyberattack, an advanced security solution is needed. That advanced security can be found in a Next Generation Endpoint Protection (NGEP) solution. In this article, we'll cover some of the issues with legacy Anti-Virus (AV), and take a look at NGEP / AI endpoint security.
How Does Endpoint Software Work?
What was once an effective way to secure endpoints in the past, no longer works today. A good security measure then was for companies to install a network firewall and AV software on each device. The AV software use definition files and signature detection to identify known threats; it is not able to detect new or unknown threats. If you are still using this security approach to protect your endpoints, your devices are at risk.
Why Is It Important to Secure All My Endpoints?
Users work on multiple endpoints, which consist of more connections to your network. These endpoints have multiple connections that extend beyond your company's Local Area Network (LAN). To access applications or subscription services in the cloud, users connect to an enterprise network or network of networks. These additional connections introduce more entry points to your network and add a higher risk of a breach to your endpoint security. A good security solution will protect your users from new, known, and unknown threat techniques. It will help you manage security across all your devices, quickly mitigate a threat, and recover from a breached endpoint.
Threats To Your Endpoint Security Software
There was a time when social engineering using a telephone was a popular method used to deceive individuals to give up their confidential information. A hacker would pretend to be a trusted source and then manipulate the user into giving up his or her personal data. Their purpose was - and still is - to steal your data with the intention to commit a fraud.
Phishing Attacks
Hackers are more sophisticated than ever before and continue their arsenal of cyberattack with new phishing techniques. Phishing techniques consist of emails sent with malicious a link. These attacks are widely used to fool users into clicking on a URL or link in an email or via social media. Phishing techniques make it possible to attack more users in less time than social engineering alone. Once a hacker has your account credentials, he or she then advances to data breach. Therefore, it's important never to click on a link, give out your personal data, or download and run an attachment or program. It is important to always verify the source, even if it's someone you think you know.
One way that you can verify your source is to call them directly. Never respond to their email as a way to verify the source. You may find that the source (e.g., employee, user, friend, family member) may have fallen victim to a baiting attack. A hacker uses a baiting attack using a reputable email provider, such as Google, to entice you with an offer and initiate a conversation. Their objective is to steal your information and fool you into transferring your funds. As phishing attacks get more sophisticated, the need for a next generation endpoint protection layer is a must.
Phishing Attacks Doubled In 2020
According to an APWG report, phishing attacks surged in January 2021 to reach an all-time high of 245,771 attacks in a single month in the history of the organization.
Survey Results
- Business e-mail compromise scams up from $48,000 to $85,000 in wire transfer requests.
- Top 3 most targeted sectors: Financial Institutions (24.9%), social media (23.6%), and SAAS/Webmail (19.6%).
- 83 percent of phishing sites us HTTPS encryption.
- More than 207k unique phishing websites detected.
Spear Phishing Attacks
Spear phishing is more selective and similar to a social engineering call where the target is a specific user. According to KnowBe4.com, "91% of successful data breaches started with a spear phishing attack." The hacker pretends to be a company official (e.g., HR manager) and sends you an email with instructions for you to send the login information for an account. These attacks are more targeted when compared to random phishing techniques.
Free Phishing Security Test
This security test allows you to find out how many of your users will fall victim to a phishing attack by clicking on a link. The test results will show you a breakdown of users that clicked on the link vs users that didn't. A free phishing security test you can run is available from KnowBe4.com. They offer a suite of free tools that you can use to test phishing and other endpoint security tests. Click here to sign up for your free test. Once you are logged in, you will be able to choose your email type.
What Is Next Generation Endpoint Protection?
What is endpoint software? The latest endpoint software in the market is Next Generation Endpoint Protection (NGEP), which prevents, mitigates, and remediates new and unknown threats in real time. Some NGEP software can act as an AV replacement while others cannot. If your business is in a regulated industry, then you'll want to add AI endpoint security on top of your existing AV software. Adding an NGEP layer on top of your legacy AV software will protect endpoints against more modern attacks. There are several players in the NGEP market: SentinelOne, Microsoft, and CrowdStrike are among them. See figure 1 for Gartner's Magic Quadrant for Endpoint Protection.
MITRE Engenuity's ATT&CK framework
MITRE's ATT&CK is short for Adversarial Tactics, Techniques, and Common Knowledge evaluations. MITRE describes its framework as “a curated knowledge base and model for cyber adversary behavior, reflecting the various phases of an adversary’s attack lifecycle and the platforms they are known to target.” This framework is the de facto standard for how NGEP products identify adversary's objectives and techniques.
Let's take a look at how SentinelOne and CrowdStrike performed on the MITRE Engenuity's ATT&CK framework simulation test.
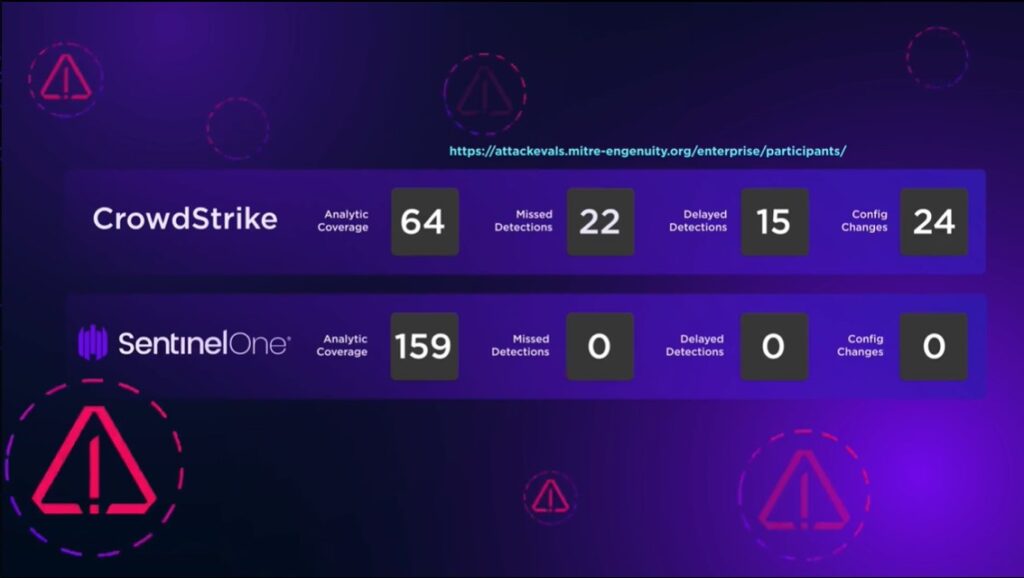
Attack Results (using Microsoft Office Exploit)
- Singularity EDR provided 100% visibility and didn't miss any detections. It tracked attacks in real time and provided the data in an easy to read view. It required no configuration changes and no delayed detections. Click here to read more about Sentinel and its full list of features.
- CrowdStrike provided 87% visibility only and missed 22 detections. Out of the 22 detections, 15 were delayed detections that took hours after the malicious activity occurred. CrowdStrike required 24 configuration changes. To read more about CrowdStrike and its full list of features, click here.
What Are Endpoints Software?
SentinelOne works in real-time mode and uses behavioral AI to analyze system behavior and characteristics. This AI endpoint security approach is used to detect and block new and unknown threats at each device. The analyzing process makes it much harder for a hacker to mask his or her attack and run a file-level execution on an endpoint.
SentinelOne Endpoint Security
SentinelOne offers dynamic malware and exploit protection, as well as forensics. The singularity platform is designed with automation to respond to threats, handle suspicious activities, and remediate known and unknown attacks. This is a big step up from Endpoint Detection and Response (EDR), which required that administrators take manual actions. What separates SentinelOne AI endpoint security from other vendors, is its behavioral AI real-time detection and protection. SentinelOne also offers a singularity endpoint security platform for identification and remediation of attacks faster and more accurately, and rollbacks of threats.
Microsoft Endpoint Security
An alternative solution to SentinelOne is Microsoft Defender for Endpoint (MDE). Microsoft provides protection that rapidly stops attacks at each endpoint. It offers extensive detection and full visibility of malicious attacks across the attack chain. MDE is able to quickly identify suspicious activity in early-stage attack and block it in real time. Click here to learn more about Microsoft MDE.
The #1 reason why you need the latest endpoint security software is because of the Artificial Intelligence (AI) feature built into this technology. Next Generation AV (NGAV) exceeds the traditional AV products with self-healing and behavior AI response that handles attacks requiring minimal or no human interaction.
About Us
Everything IT Pros is a Managed Services Provider (MSP) organization that provides managed IT services to businesses of all sizes. We offer a month-to-month subscription package and no long-term agreement. We can help you get all the services that you need, from better IT support care and security to working with your internal IT team. Our services include infrastructure, wireless networks, to AI endpoint security. We also provide digital marketing and SEO optimization of Google My Business, on-page SEO, and help your company's local ranking. Click here for more information about us.