Can Ransomware Steal Data? 3 Tips To Protect Your Business

Can ransomware steal data? Yes, ransomware can steal data - your company's data. No industry is off-limits to having their computers and data taken hostage. New ransomware techniques go beyond encrypting files and demanding you to pay the attacker to gain access to your files. The attacker is after one thing and that is your money. To increase their chances of getting paid, they parse through your data before encrypting it.
Cyberattacks have shifted from threatening with loss of access to files to public release and/or sale of confidential data if no payment is received. If you store sensitive customer information, you'll probably want to know the hidden threats of cyberattacks and the financial cost you can expect for your business. Payment demands that are often in the tens of millions. For a small business, this demand can be crippling and over 60% of companies go out of business within 6 months of being attacked.
When Was Ransomware First Discovered
When was ransomware first discovered? It was discovered over 33 years ago when the first malware (ransomware) attack occurred in 1989. The attacker's name was Joseph Popp and he wrote the "AIDS Trojan" also known as "PC Cyborg." The software was poorly written and used to collect a sum of money ($189) in exchange for the user to obtain a repair tool that would fixed the software expired message. Click here for more on the history of malware.
Who Did Ransomware Attack
Who did ransomware attack? Originally computer users in an attempt to get $189 to fix expired software. Fast forward to 2020 when the biggest healthcare provider in the US called "Universal Health Services" was attacked and their computers were locked. In 2021, a number of high-profile targets fell victim to cyberattacks, among these was Kia Motors. According to CPO Magazine, the automaker "suffered a suspected DoppelPaymer ransom attack affecting internal and customer-facing systems."
How Can Ransomware Steal Data?
Kia Motor's systems were shut down and that caused a major system and service outage for the automaker. The payment demand was $20 million worth of Bitcoin to regain access to encrypted files and avoid sensitive data leaked online. With other targets falling prey to cyberattacks, such as CNA, the question is not who did ransomware attack, but which business hasn't been attacked by malware or ransomware.
Are Ransomware Attacks Data Breaches
Are ransomware attacks data breaches? Yes, they are data breaches if the attacks are in any way connected to an "impermissible disclosure" of Private Health Information (PHI). According to Health and Human Services (HHS) "The presence of ransomware (or any malware) is a security incident under HIPAA that may also result in an impermissible disclosure of PHI in violation of the Privacy Rule and a breach, depending on the facts and circumstances of the attack." If your business is in the health field, click here for more information. Below are HHS' required security measures your organization needs to implement.
Required Security Measures:
- Implement a security management process, which includes conducting a risk analysis to identify threats and vulnerabilities to electronic protected health information (ePHI) and implementing security measures to mitigate or remediate those identified risks.
- Implement procedures to guard against and detect malicious software.
- Training users on malicious software protection so they can assist in detecting malicious software and know how to report such detections.
- Implement access controls to limit access to ePHI to only those persons or software programs requiring access.
Is Ransomware Social Engineering

Is ransomware social engineering? Yes, cybercriminals that attempt to pose as a company official (spear phishing) to infiltrate your computer and steal your data is a form of social engineering. According to Terranova Security, "Ransomware is a type of social engineering that criminals use to steal data, infect computers, and infiltrate company networks."
Is your company ready for ransomware? We've compiled an extensive checklist with vendors just for you. Click here to download our must-have 13 IT solutions every business needs. See how many of these solutions you already have in place. You'll never guess what number 5 is.
How to Protect Against Ransomware
If you've been following us and reading our blog, you would know that we are big on holistic security - that is, endpoint (laptop, desktop) security, email security, device (phone, tablet) security, and server and network security, including Wi-Fi security. Here are three tips to help you put safeguards in place against ransomware.
1. Endpoint Security
Before we can talk about endpoint security, we first need to define what it is and why it is important to have this security measure in place. Endpoint security can be a computer or device that allows a hacker to infect the computer or device and laterally spread across the network. You can't rely on other layers of security alone since they can be bypassed, for example, network security. Businesses can't rely on endpoint security alone either.
Why Traditional Security Isn't Enough
The purpose for endpoint security is to provide additional protection, filtering, and blocking of malware attacks. Without proper endpoint security, the infection or damage caused by an attack can quickly spread throughout the entire organization. Most of the time, you won't even know your systems are compromised unless you perform an audit or until the hacker strikes with ransomware and demands payment.
It is important to implement effective security layers that include real-time auditing, monitoring, alerting, and reporting. Below are areas a hacker can bypass along the way to carry out an attack. Click here to read our article on endpoint security and Next Generation Endpoint Protection (NGEP) protection. Whatever our cybersecurity stack, you want to add an Anti-Data Exfiltration (ADX) security layer.
Cyberattack Lifecycle Events
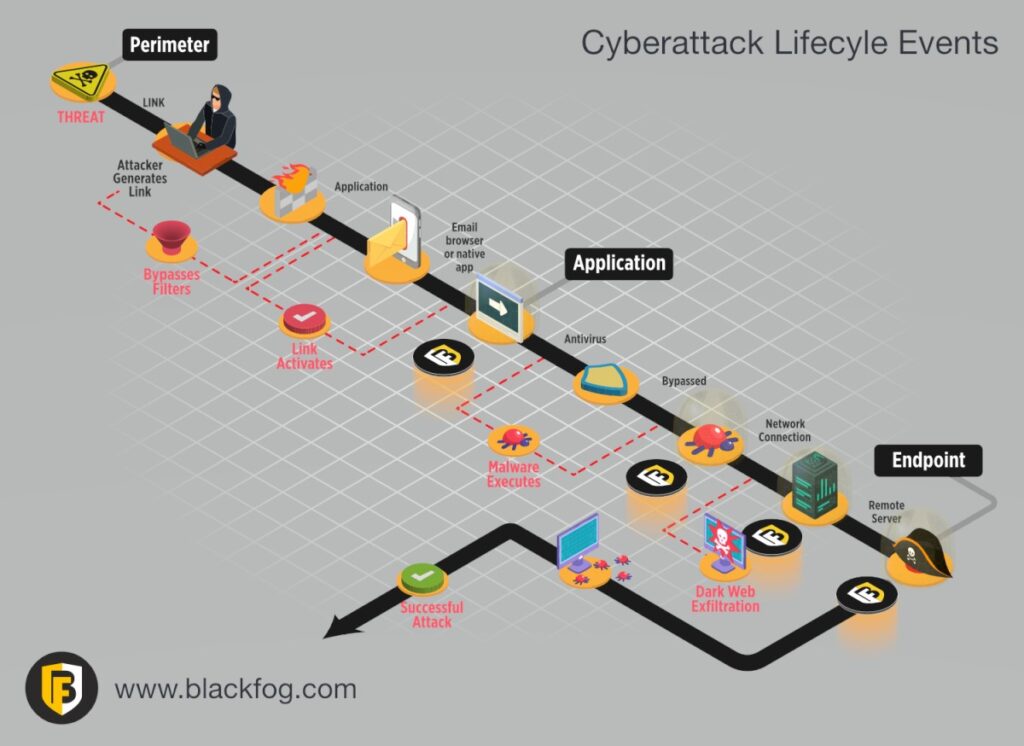
What separates BlackFog from the rest is their approach of focusing on stopping the loss of information and spread of the attack across the network. They use a feature called "data exfiltration" to neutralize the malware attacks and its reach by isolating communication and code.
2. Email Security
In an Anti-Phishing Working Group (APWG) report, the organization reported the statistics below. To learn more about the organization, click here.
- Phishing attacks in 2021 increased by double from early 2020.
- 29.1% of all attacks targeted Software-as-a-service (SaaS).
- 34.9% of all attacks were against financial institutions and payment providers combined.
- 5.6% of attacks included phishing against cryptocurrency exchanges and providers.
- Attacks on brands doubled in 2021.
As you can see threats using ransomware in emails are not going away anytime soon. Your email solution needs to be able to achieve the following:
- Block and remediate ransomware.
- Scan and detect ransomware, malware, and phishing techniques in emails.
- Prevent advanced attacks and automate response to attacks.
- Eliminate threats and the lateral spread of infection across your organization.
- Policy-based email encryption.
Two solutions we like are SentinelOne and Proofpoint. SentinelOne operates in real-time using behavioral Artificial Intelligence (AI) to scan, detect, and block new or unknown threat techniques. What separates S1 is its AI capabilities. Click here for information on Proofpoint.
3. Network Security
A network or perimeter firewall is more than just filtering and blocking inbound ports and protocols, it's about securing the traffic flow in and out of your business. With traditional firewalls, you scale by hardware, there is an annual maintenance cost, and you are responsible for updating firmware and applying updates to the operating system. Your network security solution needs to meet the following criteria:
- Network traffic control from on-premise and off-premise to cloud services and resources.
- Support policies that protect your network and Bring Your Own Devices (BYOD).
- Enforce traffic encryption across every environment.
- Protect remote workers with secure connections.
- Scalable and cost effective requiring no updates performed by you.
One of the next generation cloud firewall solutions we like is Perimeter 81. They offer scalability that grows with your business at a competitive price point. You'll be able to alter and apply policies to network traffic and define rules and control over data flow. You'll also be able to manage data flow in your environment from user traffic to network resources.
About Us
Everything IT Pros is a Managed Services Provider (MSP) that helps small and medium-sized businesses with managed services. We help organizations looking to outsource their IT to managing all the daily IT functions. We provide monthly IT powered plans and require no long-term contracts to do business. We work to earn your business every month. Our monthly subscription packages include powerful 24x7x365 security and remote worker secure connections. Call us now to see how we can make your desired outcome a reality.